You can create custom roles or use any of the built-in roles with these permissions. A way to allow computers to transmit signals over network cabling while ensuring that only one computer transmits at a time.
Security measures used for the access control systems must meet or exceed industry standards including partitioning access control privileges internal to the University.

. Access control is concerned with determining the allowed activities of legitimate users mediating every attempt by a user to access a resource in the system. Is the same concept as the multiplexing although this is a technique that can use different mechanisms. How access control policies eg identity-based policies role-based policies rule-based policies and associated access enforcement mechanisms eg access control lists access control matrices cryptography are employed by the Company to control access between users or processes acting on behalf of users and objects eg devices files records.
Implement access control procedures and secure access control systems. In todays common use this is a MAC address. Video conferences must be treated as visits under the visitation requirements of our FOCI mitigation agreement.
The objective is to assure effective media protection and controls to prevent loss or unauthorized access to NASA infonnation or infonnation systems. On any given network each device must have a unique MAC address that can be factory set when the device is manufactured or set manually. Advertisement Techopedia Explains Media Access Control MAC.
Access will be enabled only during the time period needed and disabled when not in use. The purpose of this policy is to minimize the risk of loss or exposure of sensitive information maintained by MUSA Corporation and to reduce the risk of acquiring malware infections on computers on the MUSA. What is Media Access Control Method.
CIO 2150-P-012 CIO Approval Date. Information Security Access Control Procedure PA Classification No. The MAC sublayer is the interface between the Physical layer and the LLC sublayer.
6 Code Division CDMA Do nothing to physically separate the channels All stations transmit at same time in same frequency bands One of so-called spread-spectrum techniques Sender modulates their signal on top of unique code Sort of like the way Manchester modulates on top of clock The bit rate of resulting signal much lower than entire channel. MAC is responsible for the transmission of data packets to and from the network-interface card and to and from another remotely shared channel. E Use only approved EPA removable digital media to store EPA data.
The scope of this ECP includes communications by telephone teleconference video conferences facsimile cell phones PDAs and all computer communication including emails and server access. Depending on the sensitivity of the data it needs to make certain that BD applications the MS and CSs have permissions to access the data that they are analyzing and deal. I The removable media shall be encrypted unless the EPA Deputy Administrator or Chief Information Officer has identified all data on the device as non-sensitive in writing.
Direct access to the media Distributed control over resource allocation Typically broadcast real or virtual MAC 4 Media Access Control. Media Access Control is the set of mechanisms and protocols through which various devices on a computing and telecommunications network agree to share a media the frequency range assigned to the system. This sublayer decides among competing devices on who should gain the access to the media and send data.
Advantages High data rates open new applications Low cost Local organizational control Wireless is a broadcast media and efficient use of resources is important. And having redundancy protocols in place. To access and use Removable Storage Access Control you must have Microsoft 365 E3 or Microsoft 365 E5.
Protecting against external unauthorized access. NPM will work to overcome any barriers to such ownership in FCC media ownership proceedings. Permission For policy deployment in Intune the account must have permissions to create edit update or delete device configuration profiles.
DC Official Code 1-1401 et seq provides the Office of the Chief Technology Officer OCTO with the authority to provide information technology IT services write. Media access control MAC is a sublayer of the data link layer DLL in the seven-layer OSI network reference model. At this sublayer every device is assigned an address.
Media Access Control Policy 10 OverviewPurpose Removable media is a well-known source of malware infections and can be tied to the loss of sensitive information. If two computers simultaneously place signals on the wire a collision can occur and data might be corrupted unless a method is used to resolve the collision gracefully. Access will be monitored when account is in use.
The CSO is the agency official with authority for. 09212018 ii Identify access requirements with required access levels for each system or application for authorized users to include newly assigned personnel or transfers. Lockout duration must be set to a minimum of 30 minutes or until an administrator enables the user ID.
Ii Following insertion into or connection with a non-EPA information system security personnel shall check EPA-owned USB removable media. Media Protection Policy 111. The NASA media protection policy shall be consistent with applicable laws Executive Orders directives regulations and guidance.
MEDIA ACCESS CONTROL OWNERSHIP To overcome the media divide Native Americans need increased media ownership. TSA identification media and access control media are the property of TSA. 165321 Media Access Control This sublayer which depends on a physical layer is a procedure controlled by the sender in which several devices on multidrop or bus networks compete to gain access to the medium for data transfer.
BD AC must not only enforce access control policies on data leaving the MS it must also control access to the CSs resources. And advance proposals of particular relevance to the Commissions Media Ownership priorities and rulemaking including. In some systems complete access is granted after s successful authentication of the user but most systems require more sophisticated and complex control.
Repeated access attempts will be limited by locking out the user ID after not more than six attempts. Specify requirements for minimizing risks of unauthorized access to the District of Columbia Governments District Systems and resources. 09212015 CIO Transmittal No.
They must be surrendered in accordance with DHS and TSA policies immediately upon request by an authorized TSA official or when access to TSA-controlled facilities is no longer required.

Medium Access Control An Overview Sciencedirect Topics

Media Access Control Address Cybersecurity Glossary

Media Access Control Mac Address Cyberhoot

Media Access Control An Overview Sciencedirect Topics

Media Access Control An Overview Sciencedirect Topics

Media Access Control An Overview Sciencedirect Topics
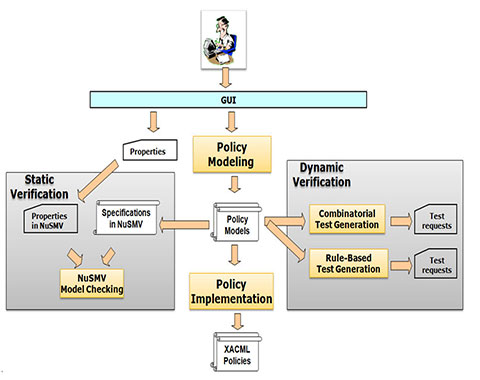
Access Control Policy Testing Csrc

Media Access Control Protocol An Overview Sciencedirect Topics

0 comments
Post a Comment